- July 13, 2020
- Posted by: Romil Lodaya
- Category: Programming

Most web applications rely on some sort of access control to keep users from accessing information not meant for them. If authentication is a lock on the main door of the hotel, then access control is the individual access card they give to each user for accessing their room.
There are several ACL methods are available like
- MAC/DAC (Mandatory/Discretionary Access Control)
- IBAC (Identity Based Access Control)
- RBAC (Role Based Access Control)
- ABAC (Attribute Based Access Control)
In this article, you will learn how you can leverage RBAC (Role-Based Access Control) feature to handle end-user authorization in your APIs.
Details of RBAC
Role-Based Access Control (RBAC) refers to the idea of assigning permissions to users based on their role within an organization. This approach provides fine-grained control and offers a simple and manageable approach to access management that is less prone to error than assigning permissions to users individually.
APIs and RBAC:
Instead of creating and storing Access for each Role in to database we have come with different way to check access for each role, which is Route based Role Access Control
EG: Let’s say we have three Roles (ADMIN, AUTHOR, and READER) in our system which is developed on NodeJS and Express.
Admin have rights to add author, delete author, approve all author’s post, delete post and read post, whereas Author has rights to create post and update own post and Reader can only have rights of reading post/articles.
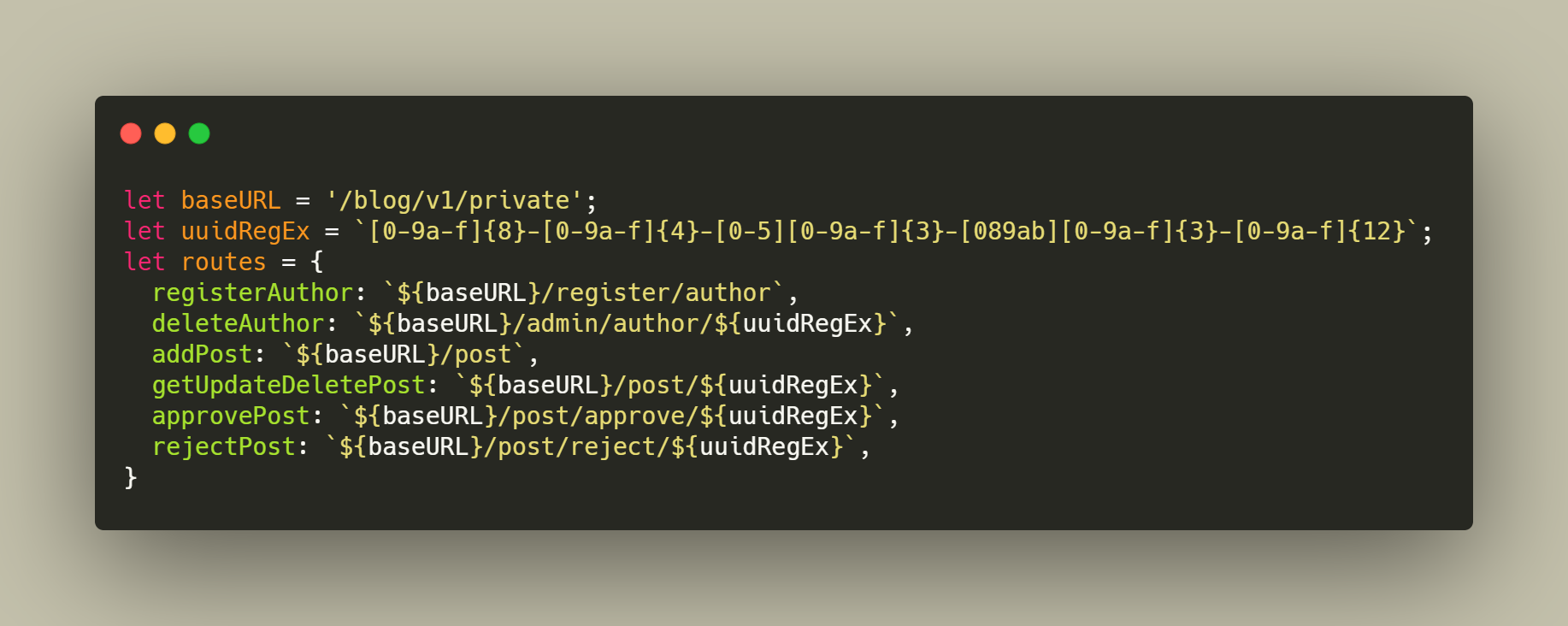
Fig 1: Routes Declaration
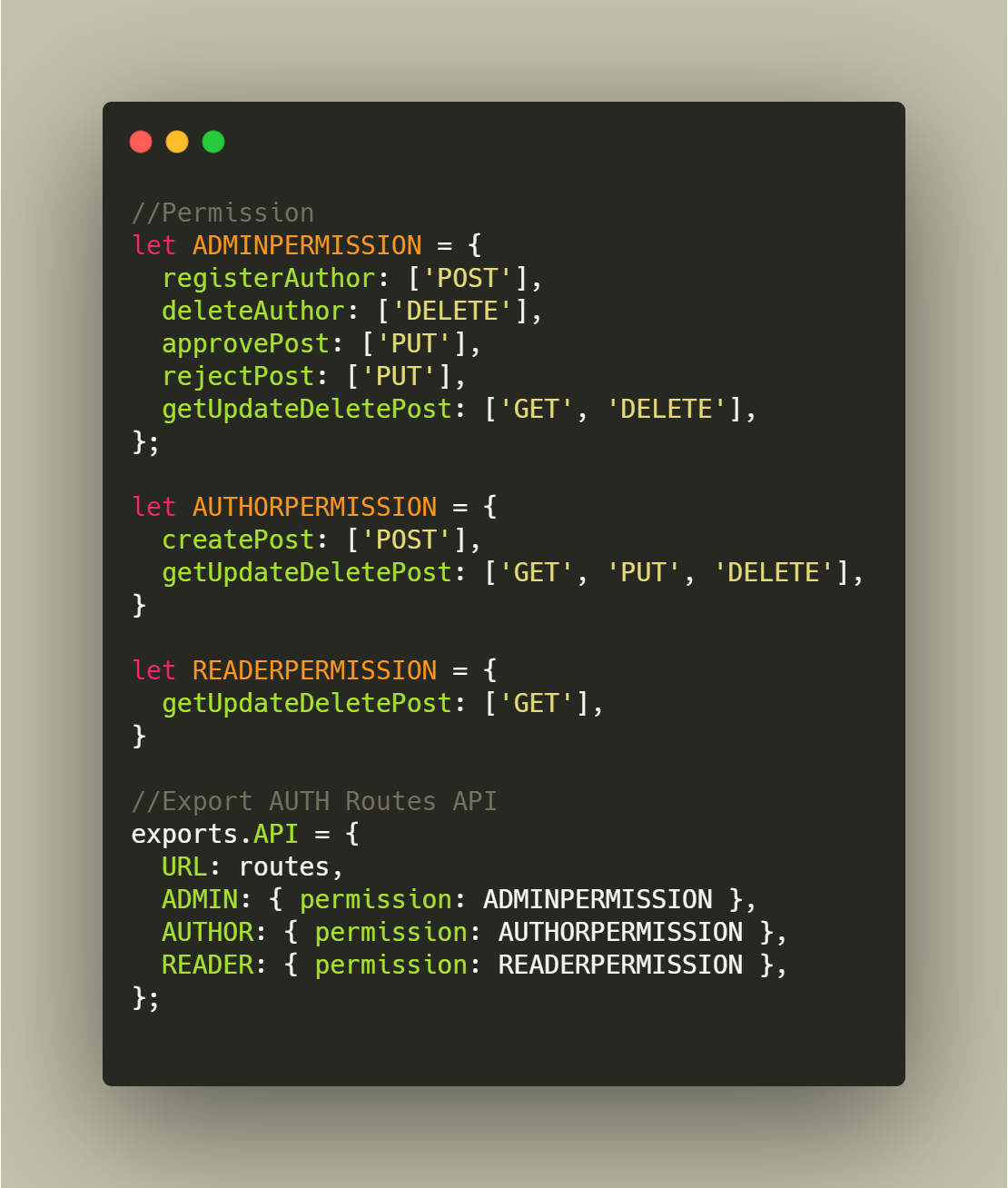
Fig 2: Permissions
In above Fig 1, we have created base URL along with UUID regular expression (We are using UUID for storing ID). In routes variable we have added all routes in our system. And in Fig 2, we have created permission according to Role in our system e.g. like In Admin permission object we have getUpdateDeletePost object key which same as routes object in Fig 1. The idea behind keeping the same object key in both routes and permission object is to find same key from routes object and based on that key again we will find incoming methods like GET, POST, PUT, and DELETE. So for admin getUpdateDeletePost have permission of GET and DELETE POST and not the update post.
When any user logged into system we are generating token along with ROLE of that user and from that ROLE we will check incoming request with method and permission that we will look into next image.
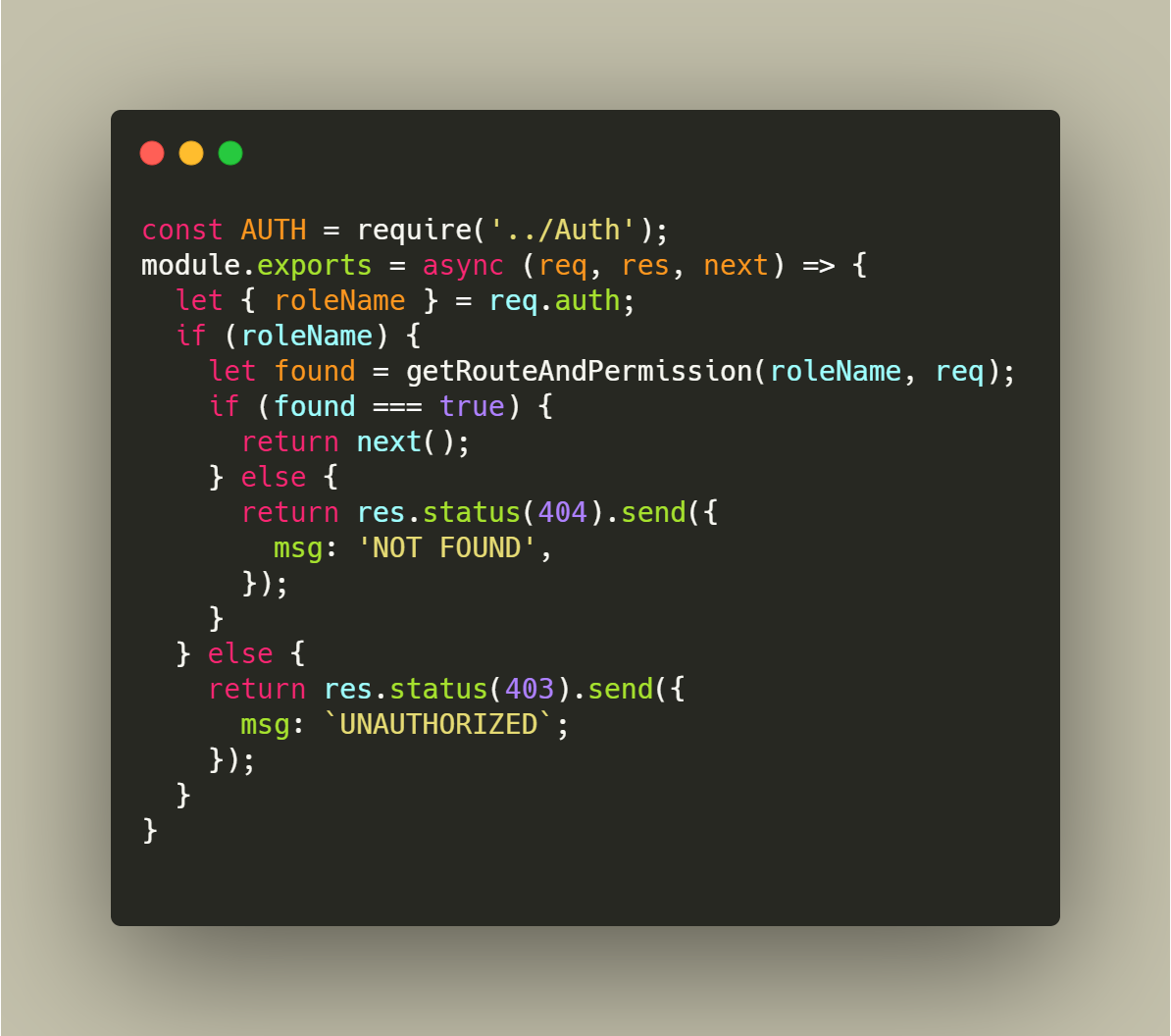
Fig 3: Route policy middleware
I have you are knowing how to add middleware in ExpressJS. In Fig 3, we have created middleware route policy named as routes.policy.js. In this first we are checking if ROLE is passed in token and if no ROLE found means UNAUTHORIZED user is accessing URL. If ROLE found pass role name and request object to getRouteAndPermission function. This function will extract method and originalUrl from request object.
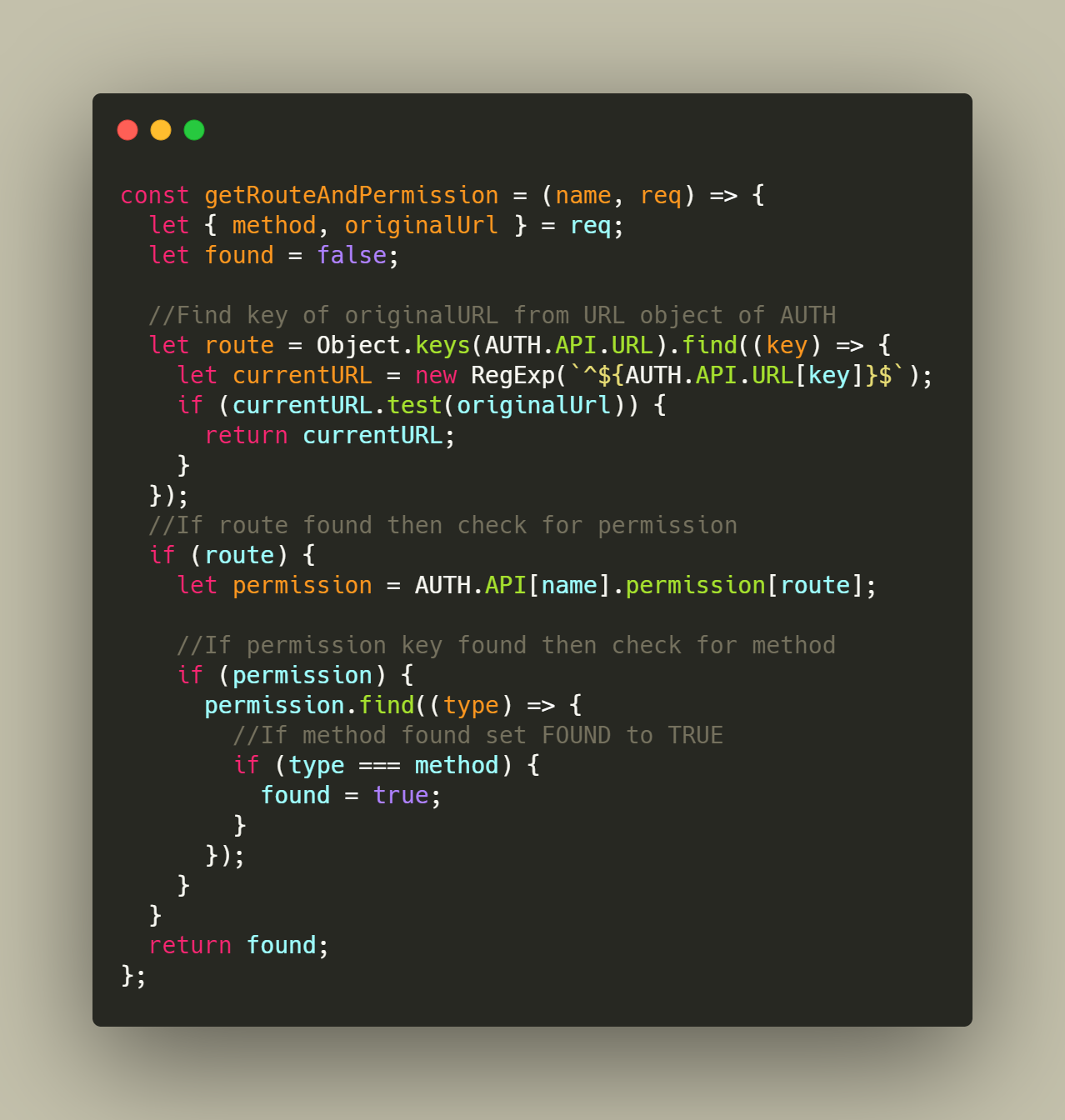
Steps to check for route and permission for that ROLE:
- First check If route is present in routes object of AUTH file
- If route found check for permission of that ROLE
- If permission found make FOUND variable to TRUE and return function with found variable and will call next() function.
- If any of the condition fails FOUND will be false and NOT FOUND along with 404 status will be response back to user.
- Fig 4: elaborates the above points.
Fig 4: Routes Permission Check
Conclusion:
Based on above implementation when you have small project you can easily implement Route based RAC without storing permission for each role into database. But for complex project or product I would not recommended this solution.